
CyberSpark excels in consulting and engineering tailored for intricate communication systems. Our dedicated team of network specialists specializes in a wide spectrum, including communication networks and fortified network security, analysis, forensics, strategy and training across diverse domains such as land-line campus networks, wireless infrastructure, and cellular networks.
Network Forensics
Network forensics is crucial in the detection and analysis of cyber-attacks through meticulous examination of network traffic. Our service objectives revolve around uncovering suspicious activities within network traffic. By leveraging advanced network behavior analysis, we identify and scrutinize abnormal traffic patterns. Employing cutting-edge analysis tools, systems, and automation, we systematically collect and analyze data to pinpoint potential security threats.
Service Objectives Include:
- Detection of Cyber Attacks: Identifying and uncovering suspicious anomalies within network traffic.
- Network Behavior Analysis: Utilizing sophisticated techniques to detect irregular traffic patterns.
- Data Collection and Analysis: Employing advanced tools and automation to gather and analyze crucial data.
Deliverables:
Our comprehensive reports not only outline detected security breaches but also offer tailored cyber protection recommendations. We prioritize empowering our clients with the necessary tools and strategies for safeguarding their networks.
Advantages for Customers:
- Detection of Security Breaches: Identifying and mitigating potential network security breaches promptly.
- Proactive Protection: Equipping clients with insights and tools to fortify their network against cyber threats
Case Study:
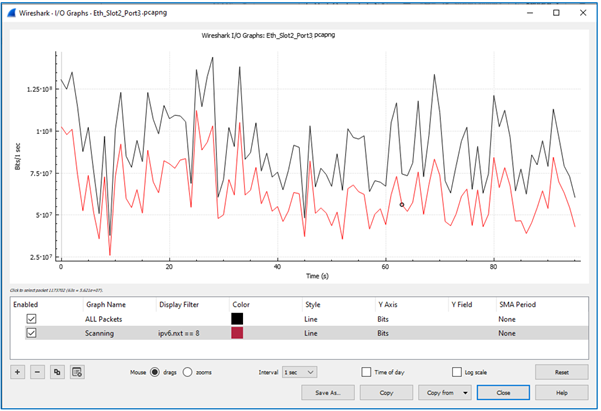
Some time back, a cellular provider suspected disruptive traffic hindering its network links to specific cell-sites. Connectivity issues arose despite the traffic not exceeding 50% of link capacities, yet consuming an excessive 80-90% without justification.
Thorough examination of customer links utilizing various tools, including the widely used Wireshark software, led to the identification of a blockade impacting their links.
Analysis of the traffic pattern revealed the presence of unidentified IPv6 traffic flooding the network in a singular direction, displaying irregular patterns and several indicators suggesting a worm infestation.
Eliminating the worm resolved the issue, resulting in a substantial improvement in connectivity to the cell-sites.



