Why Cybersecurity?
In today’s hyper-connected world, terms like Cybersecurity, Network Forensics, Secure Development, and Zero Trust are more than just buzzwords — they represent an exciting, fast-growing, and essential field that offers tremendous career opportunities.
But where should you begin? Which path suits you? Is it worth becoming an expert in one of these areas? Having worked in cybersecurity for over 30 years, I’d like to share a structured overview to help students, professionals, and newcomers navigate this field confidently.
1) The Technical Landscape of Cybersecurity
Let’s start with what actually gets attacked — and how we protect it. It’s no longer just about installing antivirus software or firewalls. Cybersecurity today involves a multi-layered ecosystem that defends everything from servers to cloud applications and IoT devices.
2) Understanding Enterprise Network Security
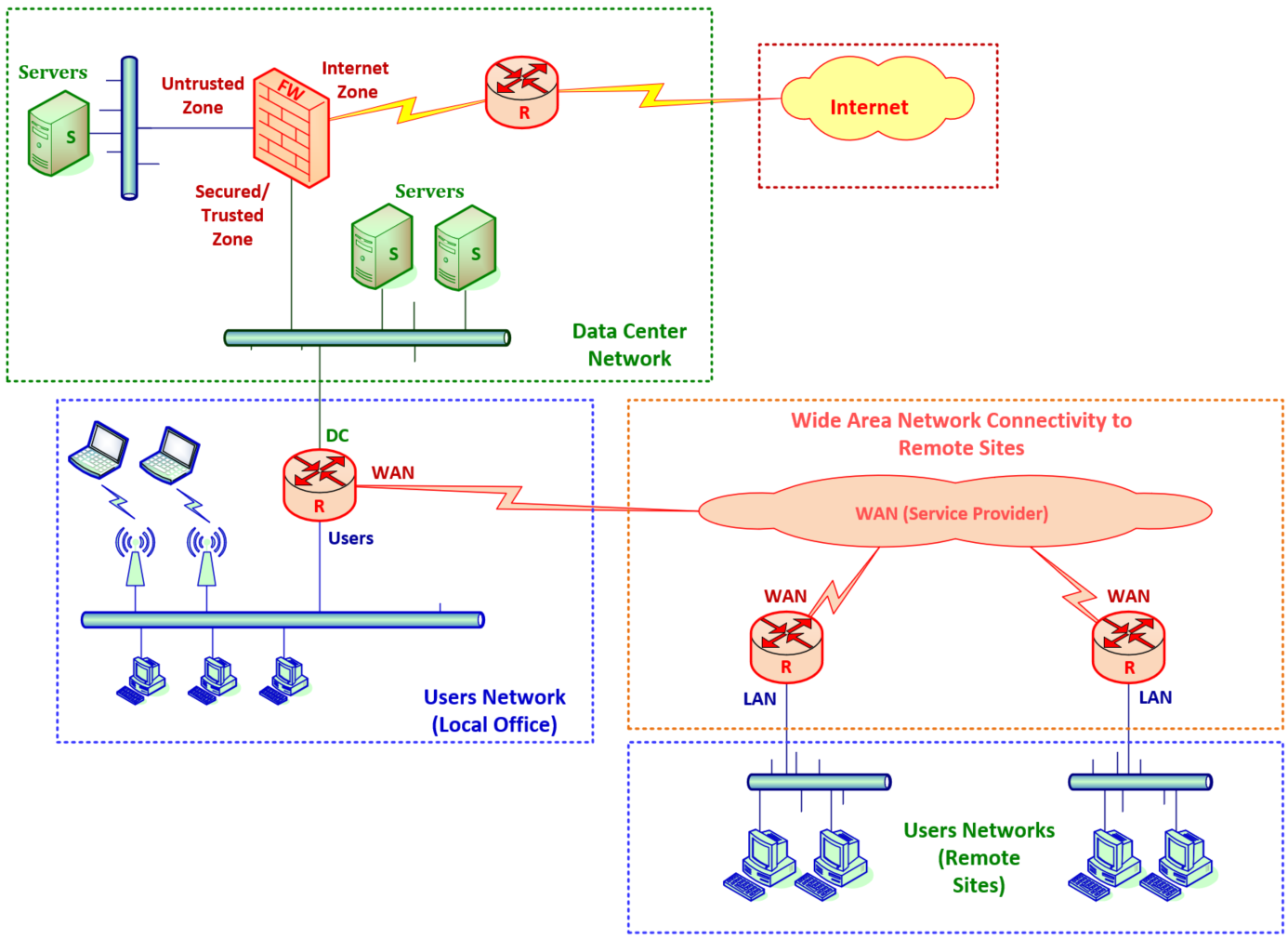
Figure 1 – Enterprise Network Structure
A typical enterprise network includes:
- Data Centers hosting critical applications on VMs or containers
- Endpoints protected with advanced tools like EDR (Endpoint Detection and Response) and XDR (Extended Detection and Response)
- Firewalls & Network Segmentation components, separating trusted and untrusted zones
- Web Application Firewalls (WAFs) guarding websites from malicious traffic
- Cloud Security and DevSecOps tools integrated into software development pipelines
2.1) Network Types:
The IT environment is sally divided into different environments:
- The Information technology (IT) environment the holds the computing resources if the administrative part of the company
- The Operation Technology (OT) that hold the Operational part of the company.
For example, in a naval port, the management, research and development, marketing and other departments that are not critical to the direct operation of the port will be on the IT network, while the cranes, container movers and other vehicles that are directly responsible for the port operation will be on the OT network.
The IT and the OT networks are in many cases are Isolated, The cyber security rules and restrictions on the OT network are much stronger than in the IT network.
2.2) Key Players:
- EDR/XDR: SentinelOne, Cybereason, Cynet
- Firewalls: Checkpoint, Palo Alto Networks, Fortinet, Cisco
- Web Security: Imperva, F5, Radware
- Secure Development: Snyk, Bearer, AquaSec
3) The Rise of IoT, Cloud & AI Threats
With IoT devices, traditional endpoint protection doesn’t work — so we monitor traffic behaviour instead. In the cloud, dynamic environments demand cloud-native security, posture management, and secure APIs. And with AI now being used by both attackers and defenders, tools are evolving rapidly. The IoT technology is usually implemented in the OT environment.
Companies like Armis and Trustwave specialize in securing these challenging environments.
4) Learning Tracks in Cybersecurity
Cybersecurity isn’t a one-size-fits-all domain. Depending on your interest and background, you can specialize in:
4.1. Research & Development (R&D)
- Focus on software, security protocols, algorithms
- Requires strong programming (C, Python, Rust), knowledge of networking, cryptography
- AI and Machine Learning are becoming integral in threat detection and automation
4.2. Engineering & Technical Support
- Involves system design, network security, troubleshooting
- Skills: Linux, Windows, virtualization, networking, firewalls, SIEM tools, cloud services
- Ideal for roles in SOC (Security Operations Center), IT security support, and infra engineering
4.3. Cybersecurity Management
- Focused on governance, policy, compliance, and risk management
- Requires understanding of regulations like GDPR, ISO 27001, NIST
- Ideal for roles like Security Manager, CISO, Risk Analyst
5. Top Certifications for Cybersecurity Professionals
Certifications validate your expertise and improve employability. Here’s what you should consider:
5.1) For R&D:
- Optional: OSCP (Offensive Security), GIAC Certifications
- Emphasis is on skills and contributions (e.g., GitHub code, CVEs)
5.2) For Engineering & Support:
- Cisco: CCNA, CCNP Security
- Checkpoint: CCSA/CCSE
- Palo Alto Networks, Fortinet NSE, Microsoft SC Series
5.3) For Management:
- ISACA: CISM, CISA, CSX-P
- (ISC)²: CISSP
- Also explore certifications like ISO/IEC Lead Auditor, CompTIA Security+
6. The Booming Cybersecurity Market in India

India’s cybersecurity sector is growing at 15–20% CAGR, with increasing government initiatives like:
- CERT-In: National cybersecurity watchdog
- Cyber Surakshit Bharat: Public-private initiative to strengthen cyber hygiene
- Digital India: Driving adoption of cloud and mobile, increasing attack surface
Homegrown Innovators:
- Quick Heal Technologies
- TAC Security
- Lucideus (SAFE Security)
- Innefu Labs
- WiJungle
Plus, India is becoming a global hub for cybersecurity outsourcing, red teaming, and SOC-as-a-service for international clients.
7. Global Trends & Opportunities
There’s a worldwide shortage of over 3.5 million cybersecurity professionals, and remote work has opened doors to global roles:
- Work for companies in the US, Israel, Europe while based in India
- Freelance as a bug bounty hunter or security analyst
- Explore niche fields like Threat Intelligence, OT/ICS Security, and Cloud Forensics
8. Ready to Launch Your Cybersecurity Career?
Whether you’re a student, techie, or mid-career professional, there’s never been a better time to explore cybersecurity. Start small. Pick a niche. Build hands-on skills. Get certified. And most importantly, connect with a thriving community.
Join Our Cybersecurity WhatsApp Community!
Get updates on:
- Free and paid training programs
- Hands-on bootcamps
- Expert talks with Israeli and Indian cybersecurity leaders
- Internship and job alerts
👉 Click here to join the community now!
Let’s build the future of cyber defense — together.
9. About India–Israel CyberSpark Academy
We are a collaborative initiative between Indian educators and Israeli cybersecurity experts. Our mission is to empower Indian students and professionals with real-world cyber skills through practical, industry-driven training and mentorship.



